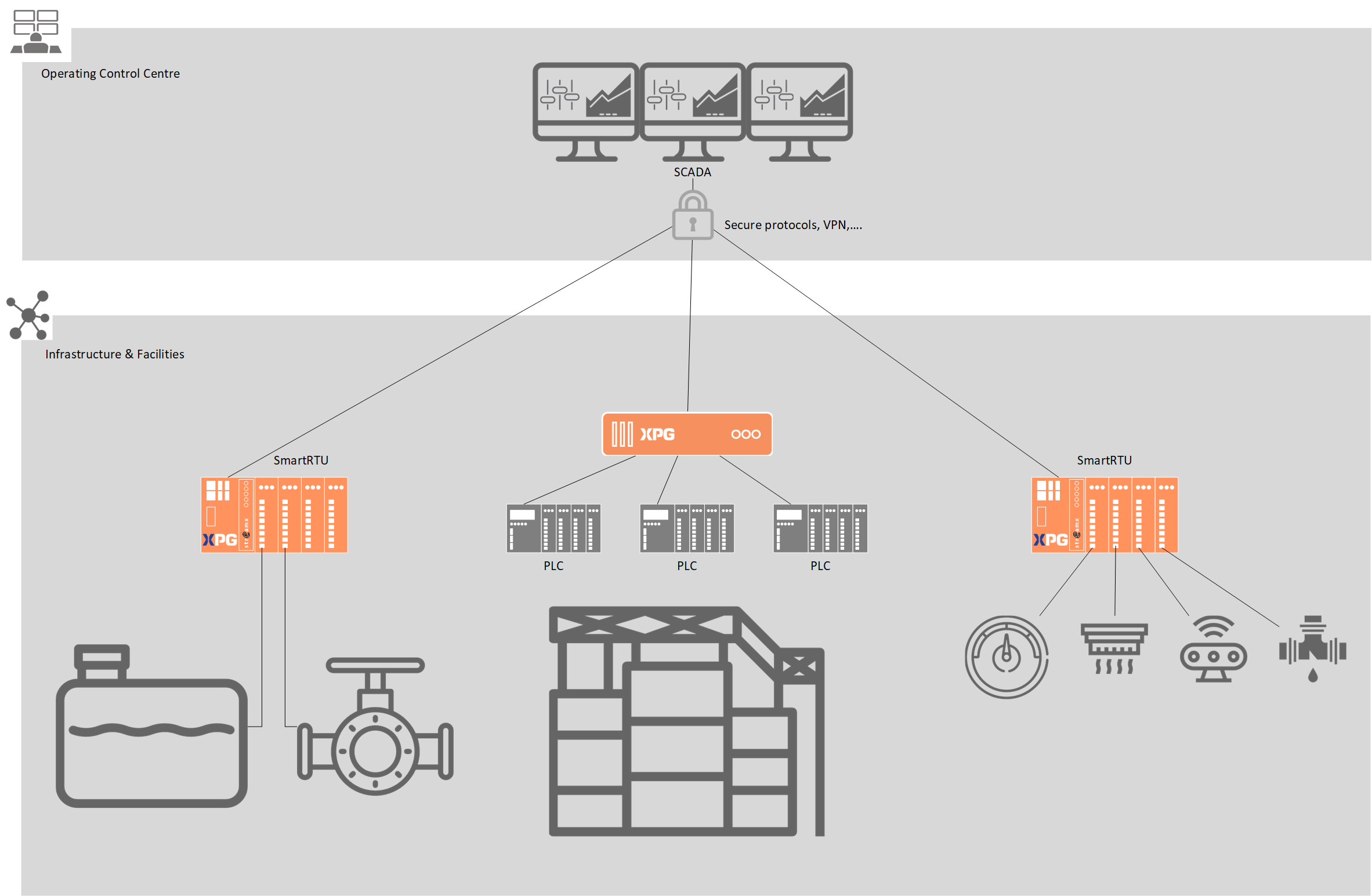
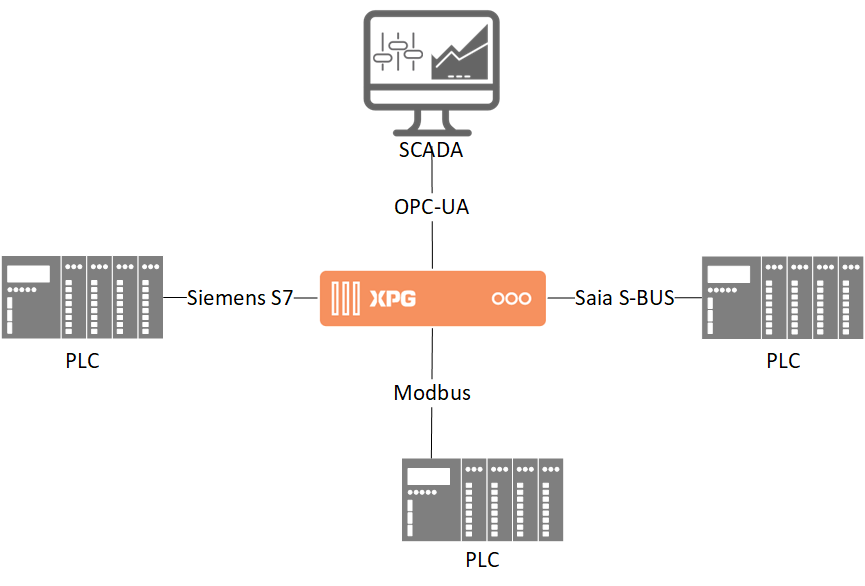
XPG – Gateway / RTU / Protocol Converter
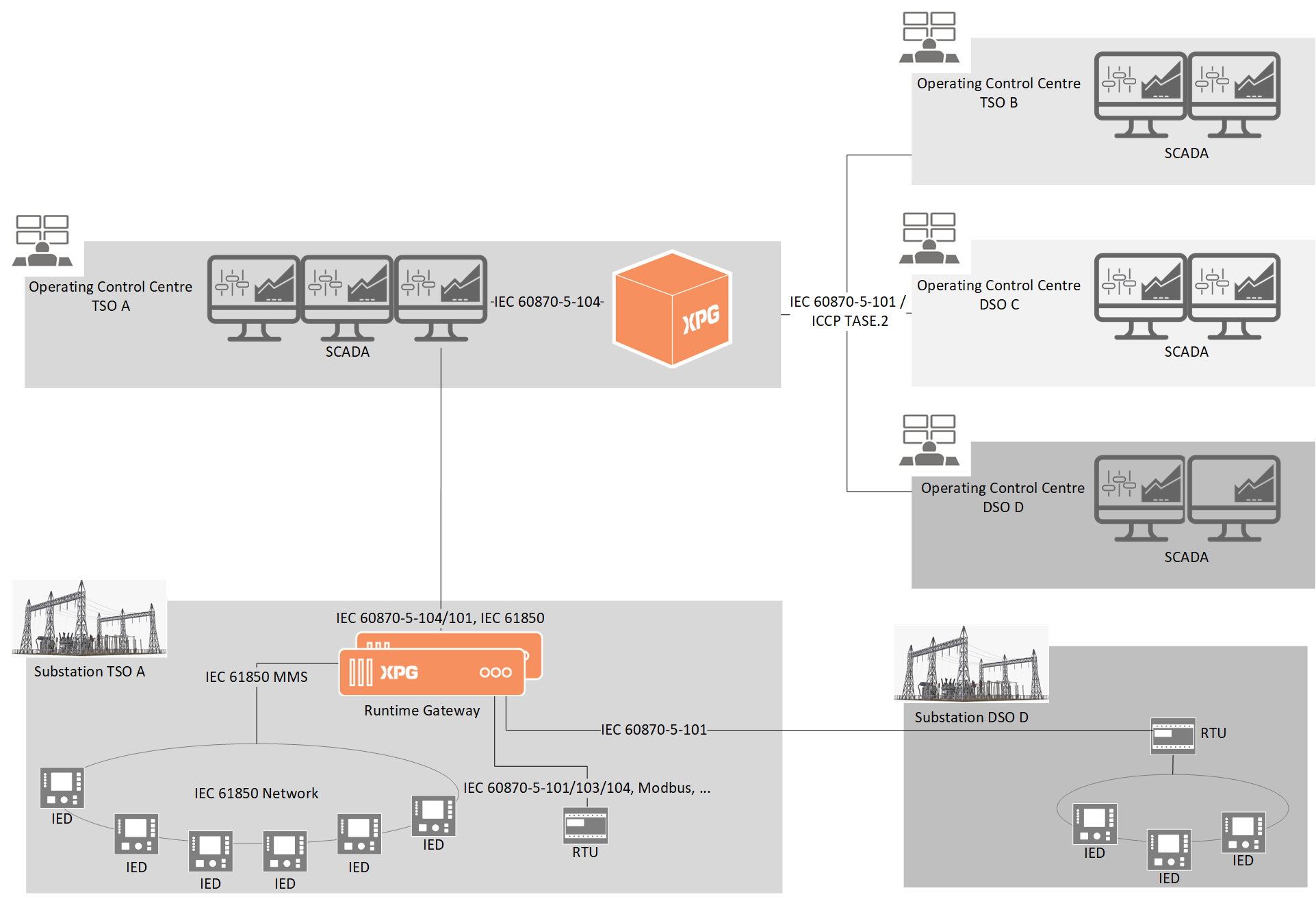
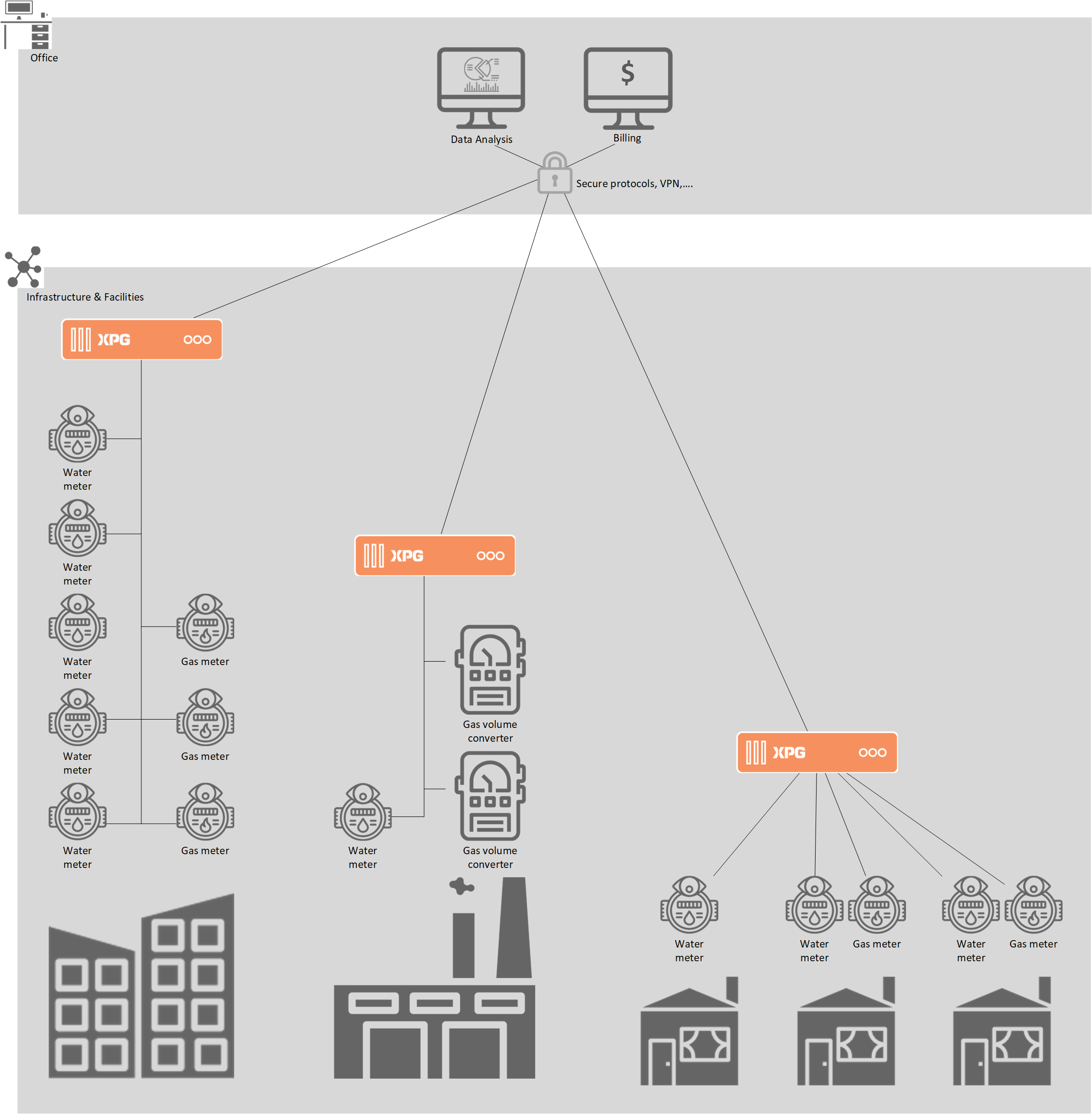
XPG is a product line used for all data acquisition, exchange, and processing applications. XPG offers multiple protocol conversion possibilities and is designed specifically for DSO, TSO, and utilities infrastructures.
XPG is based on a firmware (software solution and an operating system) developed by Elvexys. Several hardware formats as well as a virtual machine are available.
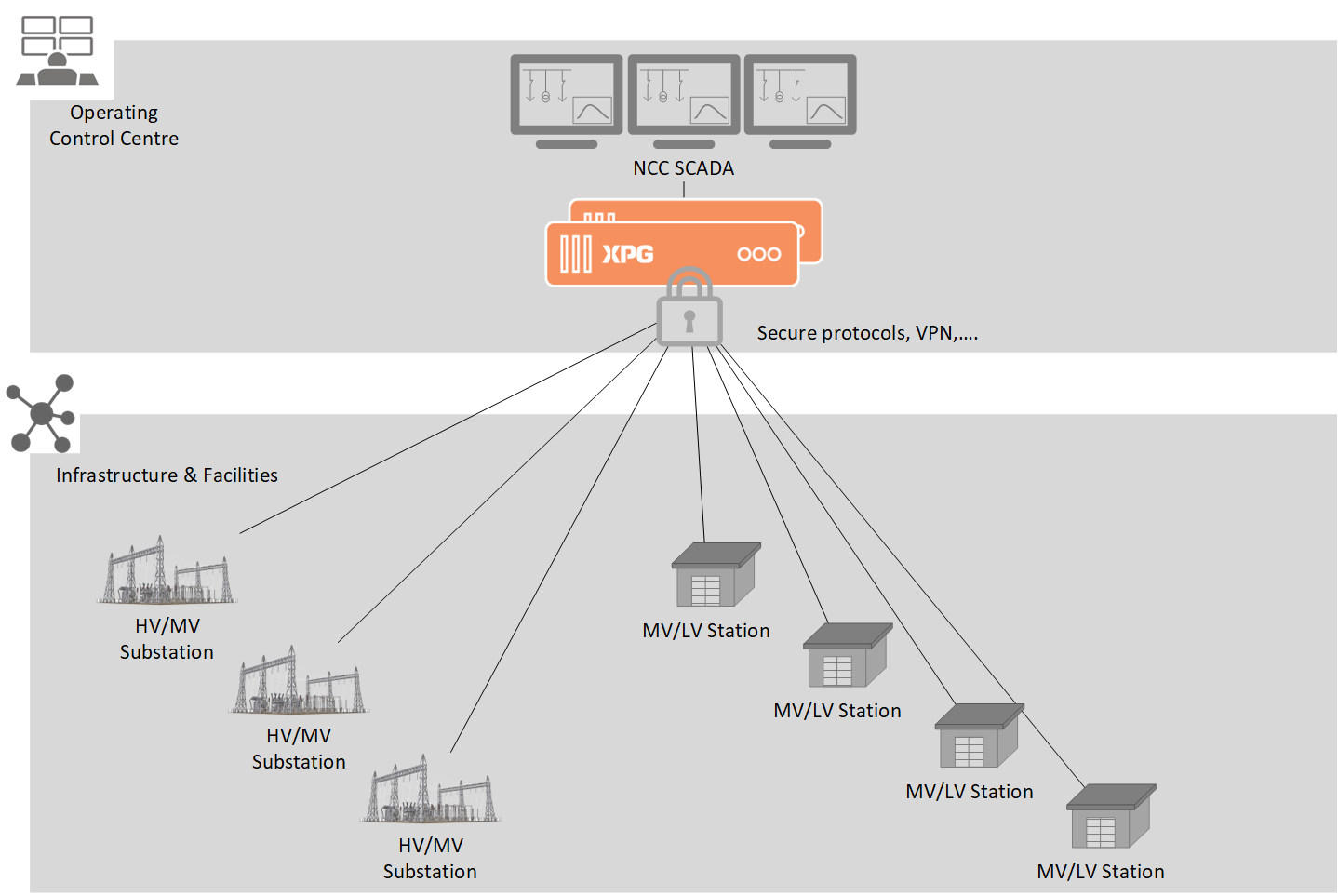
From a dozen data points in the wild, a few hundred or thousands in a substation to tens of thousands in a data centre, XPG is the scalable solution with a high level of cybersecurity that will meet your needs.
Hardware or virtual machine
Different format and mounting. Capacity, performance, and budget according to the need. With different models and virtual machine, XPG adapts to your applications.


Technologies / IT Integration
3G/4G/5G
HTTP(S) Server
LDAP Client
LDAP-S Client (TLS 1.0, 1.1, 1.2)
LoRaWAN® interface to NS
NTP Client/Server
Radius
SFTP Server
SNMP Agent (v2c, v3)
SNMP Client (v2c, v3)
SSH Server
Syslog Client
VPN (OpenVPN, IPSec)
Coming soon
CIM API
IEC 61850 GOOSE
IEC 61850 Sampled values
Kafka
OCPP
VPN (WireGuard)
Certification
XPG is certified on the standards IEC 61850 and IEC 60870-5-104 by DNV-GL
Hardware certifications depend on the model (CE, IEC 61850-3, IEEE 1613, IEC 60255, CE, FCC, EN 55032/5, EN 61000-6-2/3, EN/UL/IEC 62368-1)
Cybersecurity
Cybersecurity is at the heart of the design of XPG.
Numerous features ensure a high level of cybersecurity (Secure boot, Access and users rights, policies, VPN, port management, firewall, …).
XPG is designed to be easily monitored by IT system (SNMP, LDAP, RADIUS. Syslog,…)
To provide and maintain a high level of cybersecurity XPG follows the IEC 62443, NERC CIP, BDEW, VSE recommendations.
Our staff is continuously trained on best practices and our cybersecurity specialists closely monitor the evolution of the field and the vulnerability announcements to inform users and make swift corrections when needed.
XPG is also regularly tested and audited by utilities, TSO, or DSO cybersecurity team.